Access Control For Enterprise Security: Applications & Best Practices
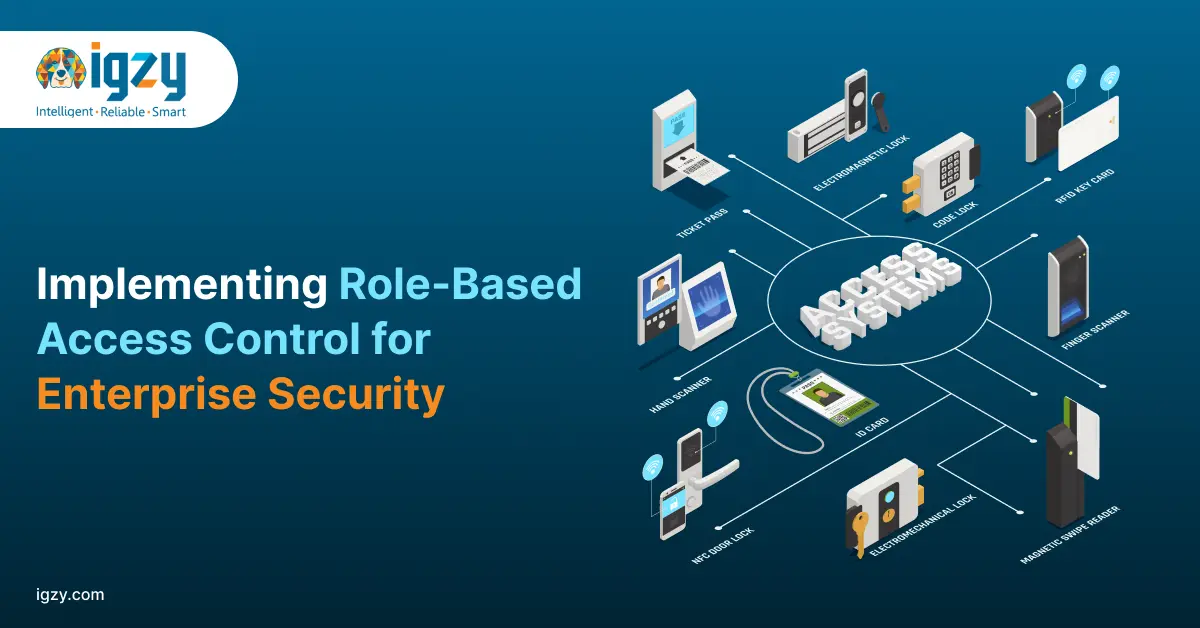
Table of Contents
Modern enterprises confront multifaceted challenges that mandate intelligent premises protection instruments. Access control systems safeguard physical and digital resources from unauthorized access. With a comprehensive access control strategy, businesses can reduce the risk of data breaches, theft, and other security incidents.
Table of contents
- What is Access Control?
- What is Access Control in Security?
- Understanding Role-Based Access Control Systems
- 4 Benefits and Features of Access Control Systems
- Industry Wise Applications of Security Access Control Systems
- Best Practices and Emerging Technologies in Security Access Control
- 4 Types of Access Control in Security
- Access Control Security: IGZY Customization SoP
What is Access Control?
Access control is a critical mechanism for ensuring that only authenticated and authorized personnel can interact with specific systems, spaces, or information. It creates a robust, multi-layered defence against potential security vulnerabilities.
Given the irreplaceable role of access control security systems in the contemporary security landscape, this guide underlines the key principles, implementation strategies, and best practices for leveraging their benefits in safeguarding premises from unauthorized entry or breaches.
What is Access Control in Security?
Access control is a security framework that governs who or what can access a particular resource. It establishes the policies, procedures, and technologies designed to manage and restrict physical or digital resource entry. This framework encompasses two key components, authentication and authorization, which ensure optimal security and compliance.
How Do Security Access Control Systems Work?
Technically, the effectiveness of access control in security hinges on two fundamental processes: authentication and authorization. Often confused, these interconnected yet distinct components form the backbone of any comprehensive security infrastructure.
Step 1: Authentication – Verifying Identity
Authentication is the initial verification process that confirms an individual’s claimed identity through multiple potential mechanisms. This can involve passwords, PINs, biometric scans, or smart cards. For example, fingerprint scanners in office premises authenticate an employee’s identity before granting entry.
Robust authentication mechanisms are crucial to prevent impersonation and unauthorized access, such as:
- Credential-Based Authentication
- It involves validating user-provided credentials such as passwords, security tokens, or biometric data
- Utilizes multi-factor authentication (MFA) to enhance security layers
- Employs advanced verification protocols like OAuth and OpenID Connect
- Biometric Authentication Technologies
- Leverages unique physiological characteristics like fingerprints, facial recognition, and retinal scans
- Provides higher security compared to traditional password-based systems
- Offers near-instantaneous identity verification with minimal user friction
Step 2: Authorization – Defining Access Permissions
Authorization determines what an authenticated individual is permitted to access. For instance, while a junior employee might have access to general office areas, a senior manager might have additional privileges to access secure zones or confidential data. Simply put, authorization determines the specific resources and actions permissible after authentication is confirmed. Key aspects of authorization include:
- Role-Based Permission Mapping
- Assigns access rights based on predefined organizational roles
- Creates hierarchical permission structures
- Enables precise control over system and resource accessibility
- Attribute-Based Access Control (ABAC)
- Dynamically evaluates multiple attributes to grant or restrict access
- Provides more flexible and context-aware authorization mechanisms
- Supports complex, nuanced access governance strategies
While several other technical approaches exist for managing access control, including attribute-based access control (grants access based on user attributes), discretionary access control (allows users to share access within predefined boundaries), mandatory access control (enforces strict, centralized access policies), and policy-based access control (utilizes pre-defined policies to determine access permissions), however, Role-Based Access Control (RBAC) remains the most widely implemented system across industries due to its simplicity and effectiveness.
RBAC simplifies access management by assigning users to specific roles with predefined permissions, ensuring a balance between security and usability.
Maximise Enterprise Security and Compliance With Analytics-Driven AIoT Solution
Your Business, Secured and Simplified
Upgrade Your SecurityUnderstanding Role-Based Access Control Systems
Role-Based Access Control (RBAC) is a security model that assigns permissions to roles rather than individual users. This simplifies access management and enhances security. By categorizing users into specific roles with predefined permissions, organizations can:
- Streamline security management
- Reduce complexity in permission assignment
- Enhance compliance and auditing capabilities
- Minimize potential human error in access management
How Does a Role-Based Access Control System (RBAC) Work?
Consider a hospital setting to understand how role-based access control systems (RBAC) work. In this scenario, various roles exist, such as doctors, nurses, and administrative staff. Each role within the hospital would be aligned as below:
- Role Assignment: Users are assigned specific roles based on job functions and responsibilities. For example, a doctor might be assigned the “Attending Physician” role, while a nurse might be assigned the “Registered Nurse” role.
- Permission Allocation: Permissions are granted to roles, not individual users. For instance, the “Attending Physician” role might have permission to access patient records, order tests, and prescribe medications. The “Registered Nurse” role, on the other hand, might have permission to administer medications, document patient observations, and access certain patient information.
- Role Enforcement: When a user attempts to access a resource, the system checks their assigned role and the permissions associated with that role. If the user’s role has the necessary permissions, access is granted. Otherwise, access is denied.
Why RBAC is Effective?
RBAC reduces administrative overhead, minimizes security risks, and ensures compliance by adhering to the principle of least privilege, which grants users only the access they need to perform their duties.
4 Benefits and Features of Access Control Systems
1. Enhanced Security
Security access control system is a barrier against unauthorized access, preventing data breaches, theft, and other security incidents. Furthermore, it minimizes the potential damage caused by human error or malicious activity.
2. Operational Efficiency
Streamlined access management through RBAC frees up administrative resources, allowing employees to focus on their core tasks.
3. Scalability and Compliance
Modern access control systems can scale with organizational growth, accommodating new users and locations. Also, many industries have specific regulations regarding data security, and access control systems help businesses comply with these regulations by ensuring that only authorized personnel have access to sensitive data.
4. Integration Capabilities
Seamless integration with surveillance, alarm systems, and IoT devices enhances security frameworks.
Industry Wise Applications of Security Access Control Systems
Access control security systems are versatile solutions tailored to meet the security demands of various industries while addressing specific operational scenarios. Here’s how these systems integrate across multiple domains:
1. Banking and Finance
- Operational Needs: Securing critical assets in banks such as vaults, ATMs, server rooms, and sensitive customer data
- Scenarios: Regulatory compliance, 24/7 monitoring and controlled access to high-risk zones like cash handling areas, ATMs and loan processing centres
2. Healthcare
- Operational Needs: Protecting patient records, pharmaceutical inventories, and medical devices
- Scenarios: Ensuring confidentiality in patient care areas and restricting access to laboratories and diagnostic zones
3. Retail
- Operational Needs: Safeguard inventory and secure point-of-sale (POS) systems from unauthorized access
- Scenarios: Controlled storeroom access, preventing shrinkage and protecting sensitive financial systems in busy retail spaces
4. Manufacturing
- Operational Needs: Managing worker access to production floors, high-risk zones, and sensitive intellectual property
- Scenarios: Enhancing safety protocols in hazardous areas and monitoring shifts in real-time to optimize productivity
5. Education
- Operational Needs: Securing student dormitories, research labs, and administrative offices
- Scenarios: Ensuring campus safety, especially in large institutions with multiple access points
6. Corporate and Commercial Environments
- Operational Needs: Visitor management and employee access control for sensitive departments
- Scenarios: Creating a streamlined, secure environment for daily operations in offices
Access control systems have transformed from mere security tools into strategic enablers, ensuring operational efficiency while addressing the unique challenges of diverse industries and scenarios. Their adaptability underscores their role as a cornerstone of modern enterprise security solutions.
Checklist: Choose the Right E-Surveillance & Security Partner
Your Guide to Selecting the Ideal Security Solution
Download free checklistBest Practices and Emerging Technologies in Security Access Control
To maximize the effectiveness of access control systems in security, organizations should adopt the following best practices and emerging technologies. Here’s how:
Best Practices
- Regularly update passwords and authentication protocols to prevent breaches caused by outdated credentials.
- Conduct routine audits of access logs to identify and mitigate potential vulnerabilities.
- Implement robust policies for onboarding and offboarding employees to ensure seamless transitions and secure access management.
Emerging Technologies
- Multi-Factor Authentication (MFA): By combining multiple methods, such as biometrics and passwords, MFA enhances security by requiring more than one verification form. For example, employees accessing sensitive systems might need to scan their fingerprints and enter a one-time password (OTP).
- Zero Trust Paradigm: This approach ensures no entity is trusted by default, even within the network. Access is granted strictly on verification and necessity. Continuous monitoring and micro-segmentation restrict lateral movement within the system, securing critical assets.
- Cloud-Hosted Solutions: Managing access control systems on cloud platforms offers unmatched flexibility and scalability. Organizations can control permissions across multiple sites in real-time, benefiting from centralized management and reduced infrastructure costs.
4 Types of Access Control in Security
Modern enterprises implement diverse access control technologies to establish secure authentication protocols and streamline facility management. Each of the below strategic systems offers unique advantages for specific operational requirements.
1. Mobile Access Control
Mobile access control solutions leverage encrypted digital credentials stored on smartphones, utilizing advanced communication protocols like BLE (Bluetooth Low Energy) or NFC (Near Field Communication). These systems integrate with enterprise mobility management platforms, enabling administrators to remotely provision or revoke access privileges instantaneously. The framework incorporates SDK integration capabilities for custom application development, supporting geofencing, time-based access restrictions, and real-time activity logging while maintaining end-to-end encryption for credential transmission.
2. Readers
Access control readers encompass hardware devices that decode credentials through multiple technologies. Modern readers incorporate multi-technology capabilities, supporting the simultaneous operation of various credential formats, including RFID, smart cards, and mobile credentials.
These devices utilize advanced encryption protocols like OSDP (Open Supervised Device Protocol) for secure communication with access control panels. High-frequency readers operating at 13.56 MHz offer enhanced security through mutual authentication and encrypted data transmission while maintaining backward compatibility with legacy systems through multi-frequency support.
3. Biometric Access Control
Biometric access control systems verify identities using complex physiological or behavioural features, including modern algorithms and machine learning capabilities to provide precise authentication. These systems analyze unique biological markers through specialized sensors, converting them into encrypted digital templates for secure storage and rapid matching during verification processes.
Key Biometric Authentication Methodologies:
- Fingerprint Recognition: Utilizes minutiae mapping and ridge pattern analysis
- Facial Recognition: Employs 3D mapping and infrared technology for enhanced accuracy
- Iris Scanning: Analyzes unique patterns in the coloured ring around the pupil
- Palm Vein Authentication: Captures subcutaneous vein patterns using near-infrared light
- Retinal Scanning: Examines distinctive patterns of blood vessels in the retina
- Voice Recognition: Analyzes vocal patterns and speech characteristics
4. Keypad Access Control
Keypad access control systems implement alphanumeric authentication mechanisms through robust PIN verification protocols. These systems integrate advanced encryption algorithms for code transmission and support dynamic PIN generation capabilities for temporary access management.
Modern keypad solutions include anti-tamper mechanisms, backlit displays for low-light operations, and weatherproof construction for exterior installations. The systems enable complex access schedules, maintain detailed audit trails, and support integration with existing security infrastructure through standard communication protocols like Wiegand or RS-485.
IGZY combines smart locks with advanced security features to enhance premise protection. The security access control system is managed via the IGZY command centre, which allows for configuring permissions based on custom SoP.
- Precision in access management: Access is granted or restricted with clear guidelines based on user roles or time-based restrictions.
- Alignment with organizational security policies: The system ensures access protocols comply with the organization’s internal security requirements.
- Scalability and flexibility: Businesses can quickly scale their access control system as their security needs evolve, adding or adjusting permissions without disruptions.
This level of customization sets IGZY apart. It offers high-level security, operational flexibility, and ease of management, providing businesses with a reliable and adaptable access control solution.
Access Control Security: IGZY Customization SoP
Access control is becoming increasingly essential for enterprises, driven by advancements in IoT and AI and the growing demand for more sophisticated and customizable security solutions. As organizations adopt more innovative security systems, IGZY leads with its tailored access control solutions for security designed to protect critical assets. Furthermore, IGZY’s access control systems stand out mainly because of their customization capabilities and alignment with global security standards.
Proven Impact for BFSI Leaders
IGZY solutions have consistently demonstrated their effectiveness, especially for BFSI leaders, including banks, gold loan institutions, and NBFCs. By adding an extra layer of protection against unauthorized access and breaches, IGZY ensures compliance, trust, and robust security frameworks within the financial sector.
A Legacy of Excellence
With over six years of successfully safeguarding industries through advanced tech-powered surveillance solutions, IGZY continues to set industry benchmarks. Our customized SoP and intelligent command centre enable precise, adaptive security management of your business landscape.
Gold Loan NBFC reports zero thefts after E-Surveillance & Cloud implementation
Improve bank security posture. Leverage advanced surveillance hardware & periodic AMC today.
Read the success story